Both Administering Windows Server 2008 Server Core and it’s more diminutive counterpart, Windows Command-Line Administration Instant Reference, are reference manuals that tell how to use the command line to perform specific tasks. The first book is more complete, in that it contains many uncommon commands and utilities. The second book is designed to provide more hands-on help by supplying a significant number of actual usage examples. In both cases, you get a significant amount of help about the commands. As long as you have one of these two books by your side, you’re in great shape for knowing how to use the commands at the command line. Unfortunately, the reality is that most of us don’t stuff a library full of books in our back pocket. Even with an e-Reader, such as the Kindle, you can be sure of having the device available every time you need it. So, how do you get at least some quick help when there aren’t any resources available?
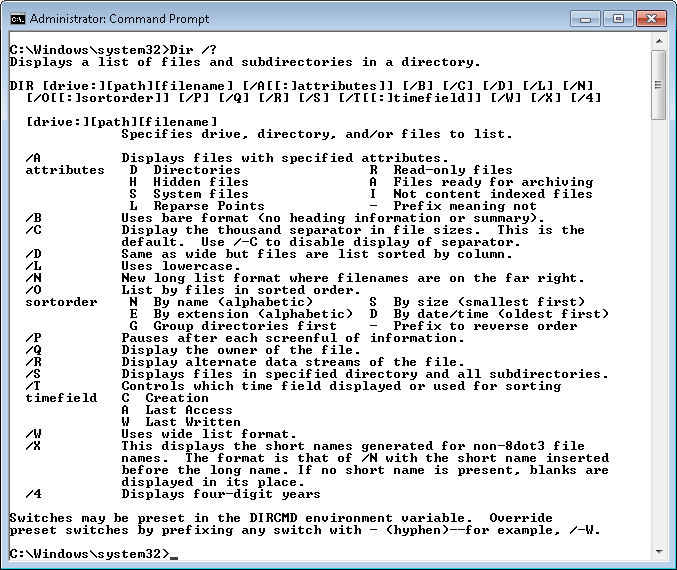
The first thing to remember is that you can get at least some useful information for any command or utility by using the /? or -? command line switches (some commands and utilities are peculiar in that they require either the /? or the -? command line switch, while many will allow you to use either). For example, when you want to discover how to use the Dir command, you type Dir /? and press Enter. Here’s typical output when using the /? command line switch.
This help screen is also typical in showing what you get. Help normally includes a short description of the command, the command line syntax, and a short description of each of the command line switches. You may also see usage examples for more complex commands. In rare cases, the help screen will provide an URL for additional help.
Some commands and utilities are complex enough that they require several help screens. For example, if you type WMIC /? and press Enter, you’ll see a list of help topics, not help of the sort provided for the Dir command. Let’s say you want to know more about the CPU topic. So, now you type WMIC CPU /? and press Enter. The help looks a little more normal now, but still isn’t very complete because you need to choose a subcommand. Perhaps you want just a list of CPUs on a system, so you request information about the List subcommand by typing WMIC CPU List /? and pressing Enter. Wow, now you see a number of listing formats. This time you add a listing format by typing WMIC CPU List Brief /? and pressing Enter. It turns out that you can also discover information about command line switches used with the Brief format. The final level in this case is to type WMIC CPU List Brief /Translate /? and press Enter. The WMIC utility is unique in providing so many levels of help, but other complex commands and utilities, such as Net, do provide multilevel help.
No matter how many help screens you see, sometimes it isn’t enough to give you the help you need. That’s when you need to find your copy of my book to get additional information. Of course, a single book can do only so much—some complex commands and utilities may require still more information. Technet is a good place to start. For example, you can find an excellent article on WMIC at http://technet.microsoft.com/library/bb742610.aspx. Knowledge base articles also provide useful information, especially when it comes to issues that Microsoft has solved for a given command or utility. For example, the Knowledge Base contains an article entitled, “How to find computer serial number” that relies on WMIC. Finally, make sure you look at third party articles, such as the one entitled, “WMIC: the best command line tool you’ve never used.”
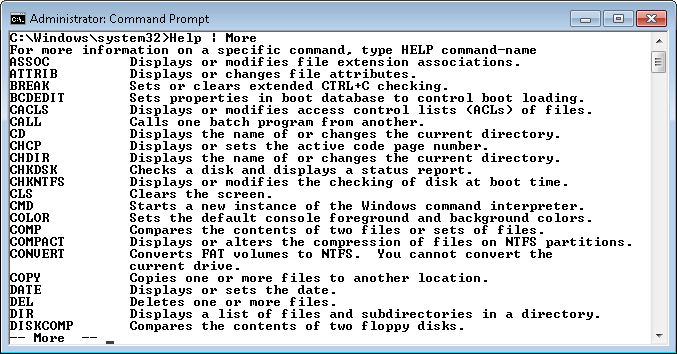
Many people complain about not being able to remember all of the commands and utilities, and this is a problem. After you use a command or utility often enough, you tend to remember it, but the memorization process can take time. Unfortunately, there isn’t any single quick method of finding every command or utility on a system. However, you should start by typing Help | More and pressing Enter. (Using the More command lets you see the information that a utility has to provide one screen at a time, rather than seeing the information scroll right past.) You’ll get a list of common commands like this one.
Not all of the commands appear on this list and none of the utilities do. Another way to obtain the information you need is to type Dir *.COM and press Enter in the \Windows\system32 directory. (You can type CD \Windows\System32 and press Enter to get to the appropriate directory.) Every directory entry you see is very likely a utility. However, many utilities are in .EXE form, so you also need to type Dir *.EXE | More and press Enter. You can eliminate files that contain more than eight letters in the filename from the list in most cases because command line utilities usually rely on the old 8.3 naming convention. Check filenames that look like they could be what you want by typing Filename /? and pressing Enter (where Filename is the name of the file you want to test). Useful command line utilities will generally display a help screen.
Now that you have a better idea of how to get command line help when you need it and where to obtain a list of useful commands and utilities, you should take some time to try it out for yourself. What techniques do you use to obtain the additional information you need at the command line? Let me know at [email protected].