On page 327 of Administering Windows Server 2008 Server Core, you find the PowerCfg utility and may not even find it all that interesting. Yes, this utility makes it possible to configure the power settings for a system from a remote location. An administrator can use it to ensure that everyone has a power saving setup by adding the command to the user’s login script. However, as utilities go, it isn’t all that interesting. For that reason, the command doesn’t even appear in Windows Command-Line Administration Instant Reference. A number of beta readers said they didn’t even use it.
Microsoft is showing an increasing interest in power management with each version of Windows. In fact, from what I’ve been reading about Windows 8, power management is going to take a relatively large leap forward (read about the changes in, “Building a power-smart general-purpose Windows“). With this in mind, the Windows 7 version of the PowerCfg utility has added four new command line switches:
- /Requests: Enumerates the application and driver power requests. Applications and drivers make power requests to ensure that resources are available when needed. However, sometimes these requests can also become a problem when they’re abused. Power requests can also prevent the computer from automatically turning the display off or going into hibernate mode, which wastes power.
- /RequestOverride: Forces the system to disregard an application or driver power request. The positive aspect of this command line switch is that you can enforce a power management strategy when you have applications and drivers that abuse power requests. However, by denying applications and drivers access to resources, you could also cause system instability or data loss when the application or driver crashes.
- /Energy: Performs an energy survey of the system. This is probably the most important addition that Microsoft has made. Using this particular feature, you can detect system elements that are consuming a lot of power and reduce its energy footprint. Generally, you use this feature with just the system running to determine what the system uses. However, you can also use it with single applications open to detect the energy cost of using that application, which I think is actually the more revealing way to use this command line switch. Most people don’t associate an energy cost with using an application. This feature makes the energy cost significantly more apparent. Yes, every application you use has a cost, so keeping needless applications open is costing you money.
- /WakeTimers: Displays a list of timers that are set to wake the system from sleep or hibernate states. Waking a system too often also costs you money. For example, it costs more to perform individual maintenance tasks at separate times than to perform them during a single time. An organization could use this command line switch to ensure that every system wakes at the same time, performs required maintenance, and then goes back into either the sleep or hibernate states.
As mentioned in the list, I consider the /Energy command line switch the most important PowerCfg addition to date. If you’re interested in self-sufficiency, as I am, then you begin to count even the pennies of energy usage. For example, in my CFLs for Free I discuss how I bought just one CFL and turned it into a complete setup for my entire home. This particular feature has allowed me to perform an energy survey of the applications I use. I found out, for example, that streaming audio using Firefox does indeed cost less than using a separate device for the purpose (such as a radio) and also delivers clearer audio. However, streaming impacts system performance and tacks a network bandwidth penalty onto other applications that rely on Internet connectivity, so there are times where using the separate device is actually better.
Let’s look at the /Energy command line switch in a little more detail. The easiest way to use this command is to open an Administrator command prompt, change directories to a directory you can write in (I’m using C:\Temp), and then type PowerCfg /Energy and press Enter. I purposely ran the command with a number of applications running and some misconfiguration in place to generate some errors, warnings, and informational messages as shown here.
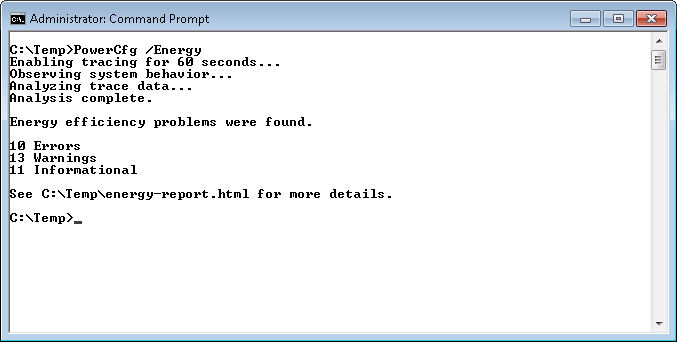
The report required a little over a minute to generate. You can see the results in the Energy-Report.HTML file. Here are the results I generated from this run.
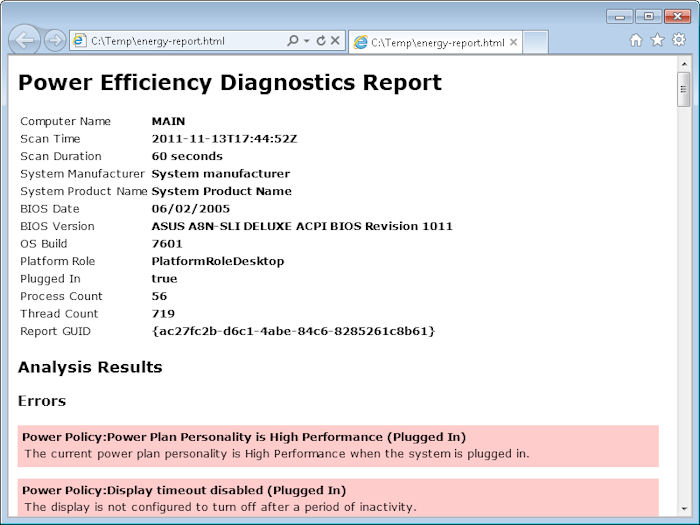
The PowerCfg utility makes it possible to diagnose energy problems with a system and significantly reduce the cost of running it. The language of the report does require a little interpretation at times, but normally the language is plain enough for an administrator to figure out with little effort. By correcting every error and 12 out of the 13 warnings, I was able to reduce the power requirements of this system by about 15 percent (as measured by a watt meter). So, how does that equate in dollars? You use the equation: Cost = ((Watts / 1000) * Hours Used) * kWh rate, where kWh is the kilowatt hour rate provided by your power company on your electrical bill. This system was averaging a little over 520 watts before tuning it. For the sake of argument, let’s say you’re using it 60 hours per week and the electrical rate is $0.12. The weekly cost of running this system is:
((520 / 1000) * 60) * 0.12 or $3.74
After tuning this one system the power usage was only 442 watts on average. That means the weekly cost went down to:
((442 / 1000) * 60) * 0.12 or $3.18
a savings of $0.56 for this one system each week or a total of $29.12 for the year. I have three systems that I tuned this way, so I’m hoping for a $87.36 savings from performing this tuning. Each system required about 30 minutes to tune, so I’ve made $58.24/hour from this activity. If you’ve read other posts, I do like to put a dollar figure on my time—you should too. Not many people can afford to throw away money like this and the PowerCfg utility, along with a watt meter, can help you better understand how your system uses (and abuses) power.
There are two additional command line switches you should know about when using the /Energy command line switch. The /Duration:Time command line switch changes the duration from 60 seconds to some other value. For example, if you want to change the duration to 120 minutes, you’d type /Duration:120. Longer testing times are often required when you’re trying to determine how an application is using energy. Take my advice and don’t set the duration lower than the default 60 seconds—you’ll be disappointed with the results.
The /XML command line switch outputs the data in XML format so that you can incorporate the information into a database. If you have a large setup, the XML format is absolutely essential. No one has time to look at individual HTML pages. Using XML output and a centralized database also makes it possible for you to look for organization-wide trends, which could produce even bigger savings.
The /Energy command line switch can also be used with the /Trace command line switch to trace energy usage without performing any analysis. This output isn’t as helpful or as accessible as using the /Energy command line switch alone. The output is an Event Trace Log (.ETL) file. To view this file, open the Event Viewer console found in the Administrative Tools folder of the Control Panel. Right click the Event Viewer folder and choose Open Saved Log from the context menu. You’ll see a dialog box asking whether you want to convert the .ETL file into the new format used by Windows 7. Click Yes. You’ll see a list of energy events like the ones shown here.
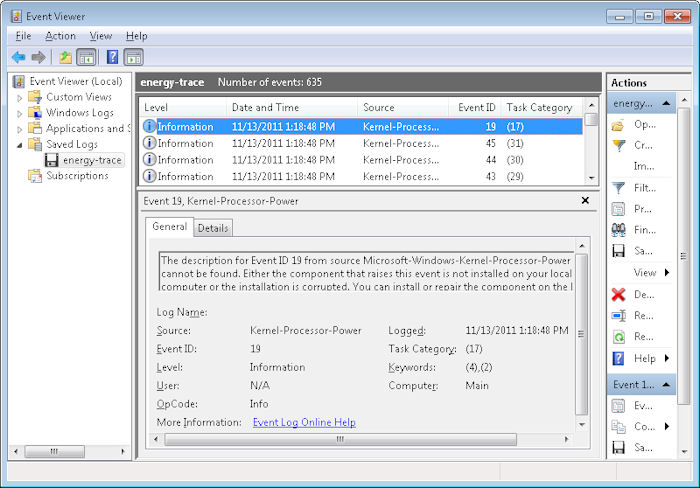
By carefully reviewing the events, you can discern energy usage patterns, filter data about specific events, and perform other analysis. However, this raw data is a little hard to use and the administrator would be better off generating the report, unless your organization has an application designed to analyze the raw data in some way.
So, how do you save energy in your organization? Do you rely on specialized tools such as a watt meter and PowerCfg? If not, how do you tune your equipment to deliver optimum service and minimum cost? Let me know at [email protected]