A number of readers have written me about the examples that use pointers in the book. One of the most common questions comes from the example on page 149 of C++ All-In-One Desk Reference For Dummies. In this example, the application contains a function that accepts an argument by reference. The use of a reference seems to have many people confused and this post will hopefully clear the issue up.
The first thing you need to understand is that there isn’t any magic going on here. The process for working with functions remains constant in C++. When you call any function with an argument, the application creates memory to hold the argument. The memory is local to that function. When the function ends, the memory is released. What the memory holds, now that changes.
Think of the memory as a box. This box has an address that points to it. When you work with a pointer, you’re working with the address. On the other hand, when you work with the value, you’re working with the content pointed to by the pointer, or the contents of the box. Whether the box the function receives contains a pointer or the value depends on how you write the function and what you pass to it from the caller.
Now, let’s look at an example so that you can better understand what’s going on. This example will do the same thing to the number each time, but using different techniques: by value, using a pointer, and by reference.
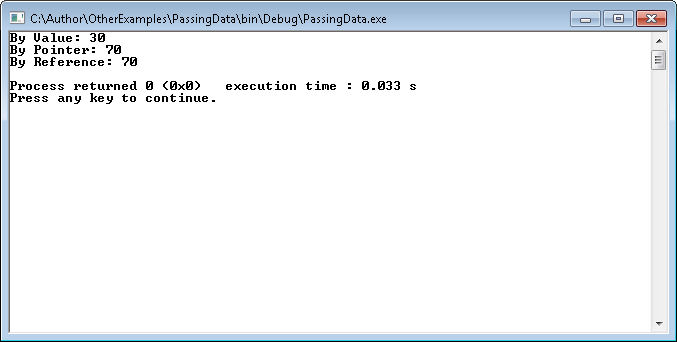
#include <iostream>using namespace std;void MessMeUpA(int myparam){ myparam = myparam * 2 + 10;}void MessMeUpB(int* myparam){ // Obtain the current value. int currentValue = *myparam; // Perform the required math. currentValue = currentValue * 2 + 10; // Save the result. *myparam = currentValue;}void MessMeUpC(int &myparam){ myparam = myparam * 2 + 10;}int main(){ // Call by value. int mynumber = 30; MessMeUpA(mynumber); cout << "By Value: " << mynumber << endl; // Call using a pointer. mynumber = 30; MessMeUpB(&mynumber); cout << "By Pointer: " << mynumber << endl; // Call using a reference. mynumber = 30; MessMeUpC(mynumber); cout << "By Reference: " << mynumber << endl; return 0;}You may notice that part of this example comes directly from page 149. If you run this example, you’ll see this output:
When you pass the data by value, you’re passing the information, not a pointer to the information. As a result, MessMeUpA() receives a value of 30. It doesn’t receive a pointer to the initial variable, nor does it obtain a reference to the initial variable. As a result, when the application performs the calculation, the result is thrown away.
When the application calls MessMeUpB(), it provides a pointer to the variable. However, the pointer isn’t a value. As a result, you move the value pointed to by the pointer into a local variable, perform the required math, and then move the value back into the original pointer. As a consequence, the original value is altered to 70.
Finally, when the application calls MessMeUpC(), the function obtains a reference to the original memory location. When the function performs the math, it’s actually using the original value as pointed to by the reference, which means that this is a kind of pointer, just not passed from the caller. The changes made in MessMeUpC() are reflected in the original value because you’re using a pointer to that value and not a copy of the value in local memory.
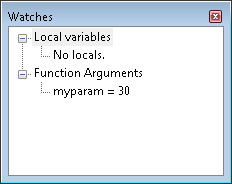
I highly recommend that anyone trying to understand how code works use the debugger to trace through that code. It’s instructive to look at each of the functions to see how they look. Place a breakpoint in each of the functions and then start the debugger. Open the Watches window, if necessary, by choosing Debug | Debugging Windows | Watches. Here is the view of the Watches window when calling MessMeUpA().
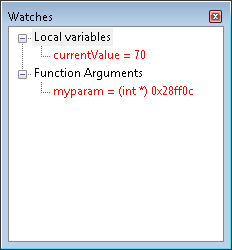
What you see here is a function argument—an integer that contains the value of 30. Now, let’s look at MessMeUpB().
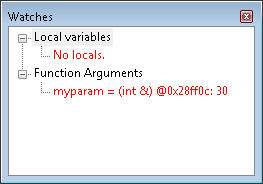
In this case, you see a local variable, currentValue, that contains the updated value and a pointer to the variable used by the caller in myparam. The pointer gives you access to the value held by the caller and allows you to change it. Finally, let’s look at MessMeUpC().
Look at the function argument, myparam. The debugger is giving you a valuable insight here. See the address provided with the variable? Match that address to the pointer provided to MessMeUpB() and you’ll see that they’re the same. The reference is simply another sort of pointer, but one that gives you direct access to the memory without having to go through the extra steps required by pointers. The debugger even shows you that the current value of that memory is 30 (the math hasn’t been performed as of yet).
A function argument is simply a box that holds either a value or a pointer. Whether that pointer is an actual pointer or a reference depends on how you write you code. That’s the point of the example. Pointers don’t have to be mysterious or hard—they’re simply an address for an area of memory (a box if you will) that holds a specific value. Please let me know if you have any questions about this issue at [email protected].