I read the security post provided by Roger Grimes with interest this morning because I’ve always felt that the Task Scheduler is just another entry point for viruses and the like on any system. As he mentions, it’s an avenue that many administrators fail to check because they don’t really think about it. As Roger points out, there are three ways to add new entries, but this post focuses on the oldest of the three, the AT command.
Before you can interact with the Task Scheduler, you must have its service started. This is a given on Vista and Windows 7, where Windows relies heavily on the Task Scheduler. However, you’ll want to read my Interacting with the Task Scheduler Service for details about this service. It’s important to have the service setup correctly in order to work with it error free.
The AT command is the oldest way of working with the Task Scheduler. At one time you could access it from the command prompt even if you weren’t an administrator. This meant that any virus or other piece of nasty software could cause woe without notice on your part. However, if you try to use the AT command at a normal command prompt in Windows 7, you’ll receive an Access Denied error message, which is at least a start in the right direction.
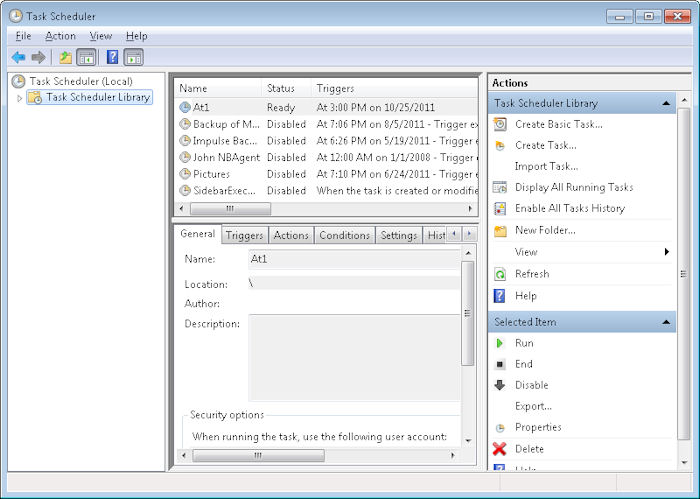
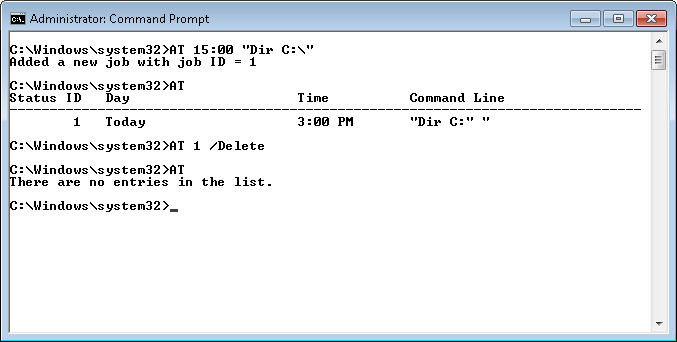
To use the AT command to create a new entry, you must provide a time and command as a minimum. For example, if you type AT 15:00 “Dir C:\” and press Enter, you’ll create a new task that starts at 3:00 pm on the current day. You’ll receive a numeric identifier for the task. The entry also shows up in the Task Scheduler console (found in the Administrative Tools folder of the Control Panel) as At plus the identifier, such as At1 as shown here.
If you want to list the jobs created by the AT command, you type AT and press Enter. The AT command only lists those jobs that it creates—you won’t see any jobs created using other Task Scheduler techniques.
Likewise, to delete jobs using the AT command, you provide the identifier you received when you created the job along with the /Delete command line switch. For example, if the identifier for the task you created earlier in this post is 1, then you’d type AT 1 /Delete and press Enter. In this case, the AT command doesn’t provide any output. In order to verify that the job is actually gone, you must type AT and press Enter. Here’s what the command output from this session looks like.
The true power of AT lies in remote access. For example, if you have an Administrator command line open, have a server named WinServer on your network, and possess administrator privileges on that server, you can type AT \\WinServer 15:00 “Dir C:\” and press Enter to create a command that starts at 3:00 p.m. (local time) on WinServer. It’s important to realize that the command will execute when it’s 3:00 p.m. on the server, not 3:00 p.m. on your system. You can likewise list and delete remote entries using the same commands you’d use for local entries. Again, the Task Scheduler console will display these entries, but only on the host machine (so you’d need to access that system remotely to see it from your local computer).
Windows 7 does make it harder to use the AT command, but not impossible. If an outsider should gain access to an account with administrator privileges, it wouldn’t take long for a virus to add all sorts of nasty commands to every machine on the network. As Roger comments in his post, administrators need to exercise vigilance in order to catch potential security issues such as this one. Let me know if you have any questions at [email protected].