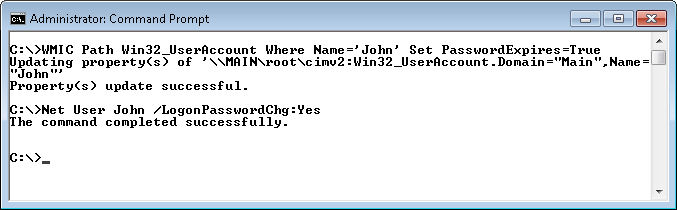
Batch files are still an important part of your system, especially if you find that you need to perform certain configuration tasks every day. Both Administering Windows Server 2008 Server Core and Windows Command-Line Administration Instant Reference discuss batch files, but this post is about a practical example of a batch file in daily use.
My system has a daily batch file. It runs every morning when I start the system up. (To save electricity, I do turn off my system every night and find that things also run better because I do.) The main reason for using a daily batch file is to configure my system so I don’t end up performing the same repetitive tasks every day. I tell the computer what to do and it performs the required configuration for me. After I get my cup of coffee, my system is ready to go—fully configured for my use.
The daily batch file appears as an entry in the Startup folder on my system. Placing the file in the Startup folder means that it runs automatically, but that I can also easily disable the batch file should I wish to do so. Use these instructions to add a daily batch file to your Startup folder:
- Choose Start > All Programs. You see a list of entries including Startup.
- Right click Startup and choose Open from the context menu. (Unless you want everyone to use the same automatic batch file, you don’t want to choose Open All Users.) You see a copy of Windows Explorer open for the Startup folder.
- Right click anywhere in the right Windows Explorer pane and choose New > Text Document from the context menu. Windows will create a new text document named New Text Document.txt—however, only the New Text Document part of the filename is highlighted.
- Highlight the entire filename and type Daily Tasks.bat. Make absolutely certain that you also overwrite the .txt part of the filename—Daily Tasks.bat.txt won’t do anything for you.
- Press Enter. You see a Rename dialog box that asks whether you’re sure that you want to change the extension of the file.
- Click Yes. Windows renames the file.
Of course, the file is empty at this point. Right click Daily Tasks.bat and choose Edit from the context menu. Windows will open a copy of Notepad with the empty batch file loaded. At this point, you can start typing commands for Windows to execute automatically when you start up in the morning. It’s possible to execute many commands directly—especially those that are meant to execute at the command line, such as W32Tm /Resync, which forces an update of the system clock. Other commands require that you use the Start command to execute them. For example, you might want to tell Firefox to automatically open the Astronomy Picture of the Day site using this command:
Start “C:\Program Files\Mozilla Firefox\Firefox” http://antwrp.gsfc.nasa.gov/apod/
<font<> <font<>The Start command starts Firefox in this case. It passes the URL you provide to Firefox as a command line parameter. Obviously, the application must support command line parameters for this technique to work. More applications than you might think do support command line parameters (many undocumented), so a little research can provide a lot in automation.
Any command that you can execute in any other batch file is also available when you’re starting Windows. There is one special consideration. You’ll likely find that executing one command immediately after another causes timing problems when Windows is initially starting. For example, if you try to open several Web sites, you’ll find that Windows actually misses opening a few unless you provide some sort of wait period between commands. Fortunately, the Choice command fulfills this task perfectly. For example, the following command provides a 15 second delay that you can insert between commands:
@CHOICE /C:N /N /T:15 /D:N
Using this command the user won’t even be aware of the delay. The @ symbol makes the Choice command invisible. The /C command line switch provides the available choices (which consists solely of N in this case). The /N command line switch hides the list of choices from view. You create the actual timeout value using the /T command line switch, which is set for 15 seconds in this example. However, the /D command line switch actuates the delay by automatically choosing N after the 15 seconds. In short, this entire command line is a wait statement.
If you want your batch to run more or less invisibly, make sure you start it with an @Echo Off command. Otherwise, every command appears in the window. It’s helpful to check for errors when you first put the batch file together and when you make changes. Adding an @Pause at the end of the batch file keeps the command window visible so you can check for errors.
After you finish the batch file, you can execute it as you would any other batch file. The only difference in this situation is that this batch file executes automatically each day because it resides in the Startup folder. When you need to make changes to this file you can choose Start > All Programs > Startup, then right click Daily Tasks.bat, and choose Edit from the context menu. The file will open in Notepad for you.
This is one of the more interesting and useful ways to employ batch files. What are your favorite batch processing techniques? Let me know at [email protected].